Yesterday I wrote about my cousin’s smart oven, and the risks of having it networked. Does this mean that you should have no IoT devices in your house? If not, how should you decide which ones are worth connecting? Here are three questions you might want to ask.
Does connecting the device to your network offer you any perceptible value?
Sometimes the answer is going to clearly be “yes”. For example, if you are taking a vacation in the middle of the winter in some cold place, you might want to know that your home’s heater broke down before your pipes froze. Having a thermostat configured to alert you to this fact might prove very useful. On the other hand, if you are in a place where such a concern is unwarranted or you would have no reason to worry about such things, maybe that same device does not need connectivity.
Will the device function correctly without connectivity?
Don’t expect an Amazon Echo to function, for instance. There is a reason why a great many IoT manufacturers are requiring Internet connectivity for their devices: the more intelligence they can move into their servers, the less intelligence is needed in the device itself, making it cheaper to build. If you are going to have a function like this in your house, this is actually an environmentally friendly way to go. Fewer parts require fewer resources used to build and to later dispose. But if a device does function properly and fully without Internet connectivy, why plug it in?
Does that device need continuous Internet connectivity?
You are unlikely to connect and reconnect your television every time you want to watch a video, but maybe you only need that thermostat connected while you are on vacation, for instance, or maybe an appliance needs a firmware update via the Internet. Occasionally connecting a device may make sense. However, take care: if you only plug in devices while you are on vacation, someone may be able to notice that and choose that time to break into your home.
Some Internet routers have the ability to block devices at certain times. Typically this is used to limit children’s access. However, one can also use these filters for other purposes. The problem is that this is nearly as annoying as having to deconfigure devices themselves. I’ll discuss this more in the near future.
Think before you buy!
The risk to your home and your privacy is real. Realistically, however, you will have some IoT devices in your house. Think about what value you derive from them, and what can go wrong if they are attacked before you buy.

 You may recall that I am working on a mechanism known as
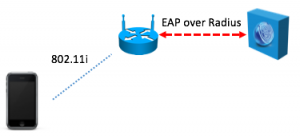
You may recall that I am working on a mechanism known as  What’s the right way to connect a Thing to your home network? Way back in the good old days, say last year, in order to connect a device to your home network, you could do it easily enough because the system had a display and a touch screen or a keyboard. With many Things, there is no display and there is no keyboard, and some of the devices we are connecting may themselves not be that accessible to the home owner. Think attic fans or even some light bulbs. A means is needed first to tell these devices which network is the correct network to join, and then what the credentials for that network are. In order to do any of this, there needs to be a way for the home router to communicate with the device in a secure and confidential way. That means that each end requires some secret. Public key cryptography is perfect for this, and it is how things would work in the enterprise.
What’s the right way to connect a Thing to your home network? Way back in the good old days, say last year, in order to connect a device to your home network, you could do it easily enough because the system had a display and a touch screen or a keyboard. With many Things, there is no display and there is no keyboard, and some of the devices we are connecting may themselves not be that accessible to the home owner. Think attic fans or even some light bulbs. A means is needed first to tell these devices which network is the correct network to join, and then what the credentials for that network are. In order to do any of this, there needs to be a way for the home router to communicate with the device in a secure and confidential way. That means that each end requires some secret. Public key cryptography is perfect for this, and it is how things would work in the enterprise.